
 Table of Contents
Table of Contents
Introduction
Operating System (OS)
- the layer of software with the application programs and users above it
and the machine below it
Purposes:
- convenience: transform the raw hardware into a machine that is
more amiable to users
- efficiency: manage the resources of the overall computer system
Operating systems are:
- activated by interrupts from the hardware below or
traps from the software above. Interrupts are caused by
devices requesting attention from the cpu (processor).
Traps are caused by illegal events, such as division by zero,
or requests from application programs or from users via the
command interpreter
- not usually running: Silberschatz's comment (p.6) that
``the operating system is the one program running at all
times on the computer (usually called the kernel),
with all else being application programs'' is wrong or very confusing --
the operating system code is usually NOT running on the processor.
However, part (or all) of the OS code is stored in main memory ready to run.
Examples of operating systems are:
- Windows Vista, Windows XP, Windows ME, Windows 2000,
Windows NT, Windows 95,
and all other members of the Windows family
- UNIX, Linux, Solaris, Irix, and all other members of the UNIX family
- MacOS 10 (OSX), MacOS 8, MacOS 7, and all other members of the MacOS family
Overall View of Operating System:
- responds to processes: handles system calls (which are either
sent as traps or by a special systemcall instruction) and error conditions.
The text sometimes refers to traps as ``software interrupts''.
- responds to devices: handles interrupts (true interrupts from hardware)
Making a Request to the OS
PROCESSES
|
| request (sent as a trap after a system call)
\|/
-------------------------------------------------------
| NUCLEUS |
-------------------------------------------------------
/|\
| request (sent as an interrupt)
|
DEVICES
Two crucial terms:
- system call:
a request to the operating system from a program;
in UNIX, a system call looks like a call to a C function, and
the set of system calls looks like a library of
predefined functions
- process: a program in execution (simple definition);
-
The operating system manages the execution of programs by
having a table of processes, with one entry in the table
for each executing entity with its own memory space.
-
Example 1: When a UNIX command such as 'ls' or 'who' is issued,
a new process is created to the run the executable file with
this name;
-
Example 2: When you select Start -> Program -> Word in Windows,
a new process is created to the run the executable file with
the name Winword.exe;
-
If two users are running the same program,
the OS keeps the executions separate by having one process
for each.
Major Services Provided by an Operating System:
1. process management and scheduling
2. main-memory management
3. secondary-memory management
4. input/output system management, including interrupt handling
5. file management
6. protection and security
7. networking
8. command interpretation
Other Services Provided by Operating Systems:
1. error detection and handling
2. resource allocation
3. accounting
4. configuration
Other Goals of OS Design:
1. easy to extend
2. portable - easy to move to different hardware
3. easy to install
4. easy to uninstall
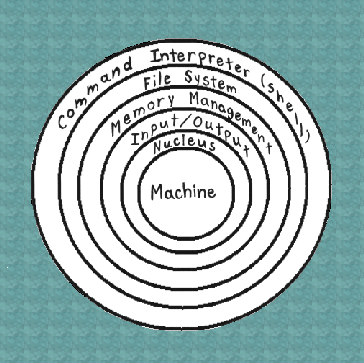
The nucleus deals with the following:
-
Interrupt/trap handling
- OS contains interrupt service routines (interrupt handlers),
typically one for each possible type of interrupt from the hardware
- Example: clock handler: handles the clock device,
which ticks 60 (or more) times per second
- OS also contains trap service routines (trap handlers),
typically one for each possible type of trap from the processor
-
Short term scheduling
- choosing which process to run next
-
Process management
- creating and deleting processes
- assigning privileges and resources to processes
-
Interprocess communication (ipc)
- exchanging information between processes
-
Within the nucleus there are routines for:
- managing registers
- managing time
- handling device interrupts
-
nucleus provides the environment in which processes exist
-
ultimately, every process depends on services provided by the nucleus
Command Interpreter or Shell
- interface between user and OS
-
used to transform a request from the user into a request to the OS
-
can be GUI or line-oriented
-
the appearance of the command interpreter is the principal
feature of the OS noted by users
-
In Windows, the command interpreter is based on a graphical user interface
-
In UNIX, there is a line-orientated command interpreter:
- a login process is first created
- a user interacts with it and the login validates the user
- changes itself into a shell process by starting to run the
executable code in /bin/csh
- the user's commands are received by the shell process as a
a string of characters, e.g. elm hamilton or
hist 20
- the string of characters is parsed and one of three possibilities
results.
-
If the first word matches
an internal command of the shell, e.g., hist, the
shell directly performs the requested operation.
-
Otherwise, if the first word is the name of a file in
any of the list of directories to be searched for programs,
e.g., /usr/local/bin/elm,
the shell creates a new process and runs this program.
-
Otherwise, an error is reported.
Layered Design
-
OS software is designed as a series of software layers.
-
Each layer of software provides services to the
layer above and uses services provided by layers below.
-
If each layer is restricted to use only the services provided by the
layer immediately below it, the approach is referred to as the
strongly layered approach.
-
Advantages:
-
easy to design and implement one layer separately from other layers (modular)
-
easy to test (debugging)
-
easy to replace particular components
-
Disadvantages:
-
hard to choose/define layers
-
slows the OS down, e.g., in a strongly layered approach
software in the highest layer (layer 5)
can only call software in the lowest layer (layer 1)
by calling layer 4, which calls layer 3,
which calls layer 2, which calls layer 1.
Virtual Machine
-
A virtual machine is a software emulation of a
real (hardware) or imaginary machine.
It is completely implemented in software.
-
A virtual machine for the Intel 8086 processor is used
to allow programs written for the 8086 to run on different hardware.
-
The user has the advantage of not having to purchase or
maintain the correct hardware if it can be emulated
on another machine. For example, if an 8086 virtual machine
is available on a Sun, no 8086-compatible processor is required.
-
Java code is written for an imaginary machine called the
Java Virtual Machine.
-
The user has the advantage of not having to purchase special hardware
because the Java virtual machine is available to run on very many
existing hardware/OS platforms.
-
As long as the Java Virtual Machines are implemented exactly according
to specification, Java code is highly portable since it can run on
all platforms without change.
Dual-Mode Operation
-
Dual-mode operation
forms the basis for I/O protection, memory protection
and CPU protection. In dual-mode operation, there are two separate modes:
monitor mode (also called 'system mode' and 'kernel mode') and user mode.
In monitor mode,
the CPU can use all instructions and access all areas of memory.
In user mode, the CPU is restricted to
unprivileged instructions and a specified
area of memory. User code should always be
executed in user mode and the OS design
ensures that it is. When responding to
system calls, other traps/exceptions,
and interrupts, OS code is run.
The CPU automatically switches to monitor mode
whenever an interrupt or trap occurs.
So, the OS code is run in monitor mode.
-
Input/output protection:
Input/output is protected by
making all input/output instructions privileged.
While running in user mode, the CPU cannot execute them; thus, user code, which
runs in user mode, cannot execute them. User code requests I/O by making
appropriate system calls. After checking the request, the OS code, which
is running in monitor mode, can actually perform the I/O using the privileged
instructions.
-
Memory protection:
Memory is protected
by partitioning the memory into pieces. While running in
user mode, the CPU can only access some of these pieces. The boundaries for
these pieces are controlled by the base register and
the limit register (specifying bottom
bound and number of locations, respectively). These registers can only be set
via privileged instructions.
-
CPU protection:
CPU usage is protected
by using the timer device, the associated timer
interrupts, and OS code called the scheduler. While running in user mode,
the CPU cannot change the timer value or turn off the timer interrupt,
because these require privileged operations. Before passing the CPU to
a user process, the scheduler ensures that the timer is initialized and
interrupts are enabled. When an timer interrupt occurs, the timer
interrupt handler (OS code) can run the scheduler (more OS code), which
decides whether or not to remove the current process from the CPU.
- Comment: although two modes are sufficient to provide the types of protection described above, a CPU can be implemented with more modes. For example, the Intel family of processors are implemented with 4 modes (called levels), which require 2 bits to distinguish them. Level 0 is the most privileged and level 3 is the least privileged (corresponds to user mode).
Other Key Concepts
-
Batch operating system:
- originally referred to the case where a human operator would
group together jobs with similar needs
- now commonly means an operating system where no interaction
between the user and their running process is possible
-
Muliprogrammed:
multiple processes in
memory at the same time, and the CPU switches between them
Types of System Calls (Silberschatz et al., p. 66):
- process control:
-
end, abort
-
load, execute
-
create process, terminate process
-
get process attributes, set process attributes
-
wati for time
-
wait event, signal event
-
allocate and free memory
- file management:
-
create file, delete file
-
open, close
-
read, write, reposition
-
get file attributes, set file attributes
- device management:
-
request device, release device
-
read, write, reposition
-
get device attributes
-
logically attach or detach devices
- information maintenance:
-
get time or date, set time or date
-
get system data, set system data
-
get process, file, or device attributes
-
set process, file, or device attributes
-
Note: As defined by Silberschatz, this category is heavily overlapped
with other categories.
- communications:
-
create, delete communication connection
-
send, receive messages
-
transfer status information
-
attach or detach remote devices

 Return to Contents
Return to Contents
 Table of Contents
Table of Contents

 Table of Contents
Table of Contents


 Return to Contents
Return to Contents