

 Table of Contents
Table of Contents
File Systems
Definition
- Reference: S&G, Chapter 10
- file system: a collection of files stored either on disk or tape
- maintained by a part of the operating system called the
file system manager
- Features of a File System
- may contain large amounts of information
- persistent: information is retained even when no process
is using it
- a file system can be accessed by many processes at once, where many
processes are between starting and finishing using files
Two Views of the File System
- Logical View (User View): abstraction of the file system presented to the user
- Physical View: how this abstraction is provided by the file manager using disks
-
Logical View of a File System
a)
- commands: create, delete, open, close, read, write, append, seek
- b)
- names for files: main.c , file.bak

- c)
- structure of the file system
- i)
- flat directory (one directory)
- ii)
- two-level directory
- iii)
- tree-structured directory (hierarchial directory)

- iv)
- acyclic graph directory structure (no cycles)

So, what happens when you use cd .. command?
Types of Linking
- a)
-
symbolic linking
- slower in use
- can link to a file whose content changes
- can link across file systems (and machines under NFS)
- In UNIX, adding a symbolic link has no effect on the original
file and in particular has no effect on the linkcount
- if person A creates a file and person B links to it, when A
deletes it, the link fails when B tries to use it
- Example:
% ln -s /usr/w/h usr/local/h
% rm /usr/w/h/
% cat /usr/local/h
UX:cat: ERROR: Cannot open /usr/local/h: No such file or directory
- b)
-
hard link
- creates a new ``true name'' for the file
- the file is only removed when no links to it remain
- you create the file, set linkcount (stored in i-node) = 1
- someone links to the file so linkcount = 2
- you delete the file, so linkcount = 1 but the file is kept
- complication: you own a file that you no longer have any
access to
- Example:
% ln /usr/w/h /usr/local/h
% rm /usr/w/h
% cat /usr/local/h # still works because file still exists
Access Control (File Protection)
- Reference: S&G, Section 10.4 and Chapter 13
- each domain defines a set of objects (i.e., files) and the types
of operations that may be performed on each object
- in the simplest case, a domain is a user
Some Privileges

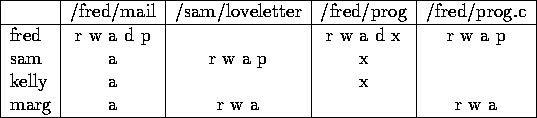
Example Access Matrix
Other Privileges from S & G

Capability List
- for every domain, list the objects and their privileges (only
objects for which the subject has some privileges)
/fred/mail /fred/prog /fred/prog.c
fred





/fred/mail /sam/loveletter /fred/prog
sam





/fred/mail /fred/prog
kelly



/fred/mail /sam/loveletter /fred/prog.c
marg




Access List
- for every object, list the domains and their privileges (only objects for
which the subject has some privileges)
fred sam kelly marg
/fred/mail







sam marg
/sam/loveletter



fred sam kelly
/fred/prog
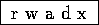




fred marg
/fred/prog.c



In UNIX:
- We classify the users into three catagories.
- Thus, from each user's perspective, there are three domains.
- Simplified access list:
- u = user (me)
- g = others in my group (group)
- w = any other user (world)
me mygroup others
file







 Return to Contents
Return to Contents
 Table of Contents
Table of Contents


 Table of Contents
Table of Contents








































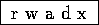
















 Return to Contents
Return to Contents